Keep your employees and data safe
Digital transformation, cloud, and mobility have driven information technology to a crossroads—and security architectures to the breaking point. As a result, organizations struggle to empower mobile workforces, maintain applications, and properly protect data as it flows between environments. Traditional approaches to data protection tend to be rigid, limiting enforcement to permit or block only. This leads to an endless cycle of alarms and alerts, as security teams struggle to identify, triage, optimize system policies, and remediate true risk. The good news is now there’s a smarter way to safeguard critical and sensitive data, no matter where it lives or travels. By integrating behavior-centric analytics with data protection tools, Forcepoint allows you to prioritize high-risk activity and automate policies to protect data in near real-time, providing the highest security and workforce productivity

Forcepoint Secure
Web Gateway
Stop advanced threats hidden in dynamic web content
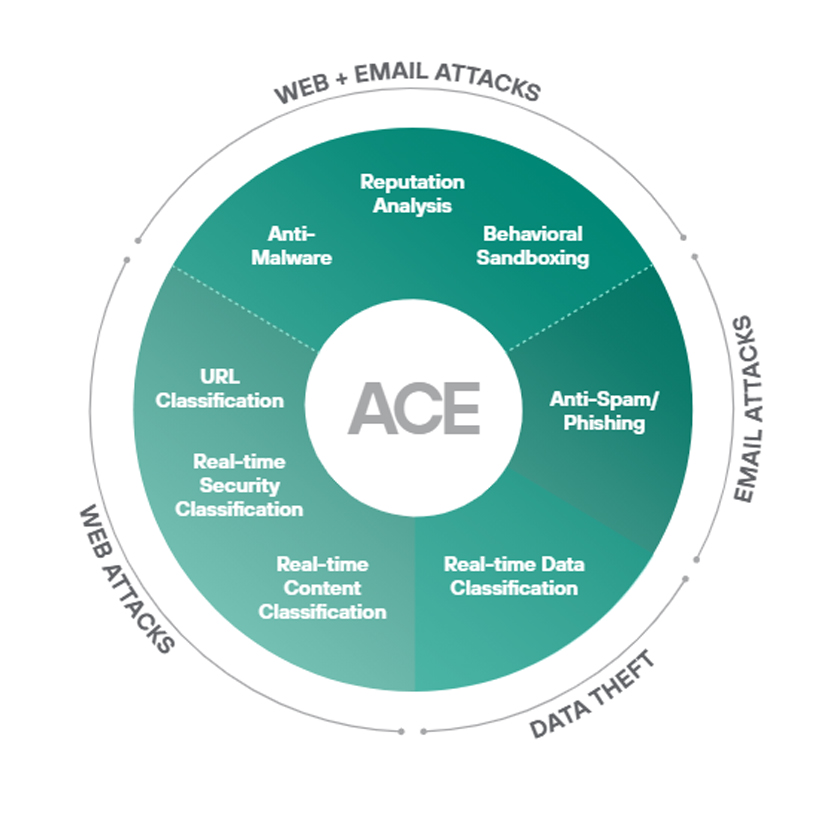
Web Security Objectives:
Any device, any cloud, any app
Behavioral analytics and inline capabilities secure your policies and data across the world
Safe access for every user, anywhere
Consistent policies with robust access control for all your sites, cloud apps, and users — both on and off the corporate network.
Move to the cloud at your own pace
Choose when, where and how you deploy. Choose where and how you connect to the cloud.
Industry's most secure cloud infrastructure
Global access points for faster local connectivity with over 160 PoPs across 145 countries.
Advanced threat protection powered by ACE
Keep users safe from malicious threats, including zero-day threats. Protect against zero-day threats with real-time threat intelligence and remote browser isolation, and provide deep content inspection for encrypted and unencrypted traffic to detect evolving threats across the entire kill chain.

Forcepoint Data Loss
Prevention (DLP)
Secure your data without slowing down your business
Safeguard your organization’s critical data and IP and help ensure compliance while providing frictionless, secure access to data from wherever your employees are.
Secure regulated data with a single point of control for all the applications your people use to create, store, and move data
Protect intellectual property with advanced DLP that analyzes how people use data, coaches your people to make good decisions with data, and prioritizes incidents by risk
Stop the breach before it happens:
Shift from event-centric to risk-centric approach with real-time enforcement.

